SECURE CLOUD TRANSFORMATION
THE CIO'S JOURNEY
By Richard Stiennon
Introduction Section 1: Transformation Journey Chapter 1: Mega-Trends Drive Digital Transformation Chapter 2: Moving Applications to the Cloud Chapter 3: From Hub-and-Spoke to Hybrid Networks Chapter 4: Security Transformation Section 2: Practical Considerations Chapter 5: Successfully Deploying Office 365 Chapter 6: A Reference Architecture for Secure Cloud Transformation Chapter 7: Perspectives of Leading Cloud Providers Section 3: The CIO Mandate Chapter 8: The Role of the CIO is Evolving Chapter 9: CIO Journeys Section 4: Getting Started Chapter 10: Creating Business Value Chapter 11: Begin Your Transformation Journey Appendix Contributor Bios Author Bio Read Offline: Open All Chapters in Tabs eBook Free Audiobook
Free Audiobook
 Hardcover
Hardcover

Chapter 10
Creating Business Value

““We moved 75 percent of our infrastructure to the cloud over about a three-year period for a savings of $100 million a year. We were then able to devote that savings back into things that mattered to our business.”
Stephen Orban, General Manager, Amazon Web Services

The Power of Cloud Economics
One of the main drivers to cloud computing is the ability to right-size services and resources based on requirements and varying demands. In the cloud, enterprises pay for what they use and scale their investments with usage as their business needs evolve. Conversely, if demand decreases and capacity is no longer required, the cloud gives enterprises the ability to turn off systems, and they are not charged for underutilization. This model is vastly different than the traditional on-premises paradigm which was capital intensive as it required enterprises to pre-plan and procure additional capacity in anticipation of growth. In the pre-cloud world, IT organizations were also required to invest heavily in the day-to-day management and maintenance of their data centers and branches worldwide, placing tremendous pressures on enterprise CIOs to continue to innovate and grow, while grappling with the rising costs of IT.
Cloud transformation is disrupting both traditional and emerging business models and creating new opportunities for the enterprise. It is forcing IT to shift its mindset from being a service provider to a value broker, creating more efficient and cost-effective ways of conducting business to boost productivity and stay agile.
The move to the cloud often involves three transformation stages: application, network, and security transformation. When planning transformation steps and evaluating the financial investments and associated returns on those investments, it is important to note that application transformation savings can vary dramatically based on the type of applications being migrated or transformed. However, the cloud economics associated with network and security transformation is relatively straightforward to quantify. The rest of this chapter will focus on creating economic value for your business through network and security transformation.
Here are some data points that illustrate why legacy on-premises economics fails in this new world:
- A typical enterprise organization sees more than 50% of its WAN traffic destined for the internet, whether that’s recreational or business usage, cloud, and SaaS. To add to that, the average compound annual growth rate (CAGR) for internet consumption is predicted to be 30% and you have traffic volumes that legacy network architectures were just not designed to handle.
- The cost of bandwidth is fast declining as internet usage on your network continues to increase exponentially. However, adding more bandwidth to offset legacy architecture limitations does little to address the escalating user performance concerns. Your legacy network topology and architecture has now become a bottleneck to delivering the very promise of cloud applications—improved productivity and enhanced user experiences.
If your WAN links are already predominantly carrying internet traffic and that traffic is anticipated to double in the next three years, are your WAN links really much more than expensive internet circuits? Moreover, aren’t your data centers becoming just another hop to the cloud, where many of your applications now reside?
As we have learned through the experiences of many of the journeys in this book, this was typically the pivot point when they realized that the internet was becoming their new corporate network and the cloud, their new data center. This new dichotomy put them on a path to evaluate the options available and to carefully consider the technological, organizational, and financial imperatives of cloud transformation.
Evaluating your Transformation Costs
At this stage, you have probably begun the process of evaluating your cloud transformation options. What next? For the highest chance of success, your network transformation efforts should provide the most direct path to resources on the internet, and present immediate and long-term cost savings options. As we have highlighted in Chapter 4, to achieve this outcome you will need a cloud-native security service that allows you to leverage local internet breakouts while removing the cost, complexity, and risks associated with deploying local security at each branch. With this strategy, you will be able to transform as many branches as your organization needs through your cloud journey while providing your employees at every branch with the required security capabilities and superior user experience, all the while helping keep your future costs flat.
In prior chapters, we’ve also highlighted that the focus of the new model is the user and not the number of locations you need to support. In this new model, you now have the power to migrate branches and users away from centralized gateways based on the priorities you define, and without incurring additional costs or changes in policy and security.
Expecting a 30% increase in internet traffic requires IT teams to plan regular upgrades to meet this change in demand. These upgrades usually encompass three key components: security appliances, internet (ISP) bandwidth, and WAN bandwidth. Planning for growth in these areas is nothing new to IT professionals as they have regularly had to plan for regular increases in traffic. The significant difference between today and five years ago is just how critical the role of the internet has become in day-to-day business. Planning for scheduled cutovers or holding off on necessary upgrades could be materially disruptive to the business.
Properly planned and executed, your secure cloud transformation eliminates the need to upgrade all three components. Here’s how:
Security Appliances
Transformation with a cloud security architecture mitigates the need to scale appliance footprints and, in many cases, eliminates the need for appliances completely. Appliances are sized around throughput, and the only way to scale is to add boxes or by refreshing to higher capacity boxes. Unless your current appliances are running at only 20% utilization, which is highly unlikely, you are looking at increasing your capacity in the next two to three years. This applies to every inline security appliance in your stack: IPS, firewalls, proxy, SSL decryption, and so on. With local internet breakouts, you’re diverting traffic away from large internet gateways to your cloud security service. In this new paradigm, scale is no longer a problem, and there is no need to plan for upgrades to your security appliances, resulting in a straightforward future-cost avoidance win.
Once you’ve broken out branches, you can retire your internet gateway appliances, in favor of a single admin console. That means eliminating your annual OPEX spend on hosting facilities, vendor maintenance, licensing, and support, and eliminating the CAPEX required to purchase and refresh hardware. It also helps avoid the need to hire experts to support the latest security capabilities your company needs to remain secure in this ever-changing threat landscape.
Internet Bandwidth
As the majority of your users become mobile and the applications they utilize move to the cloud, and as more and more of your traffic becomes internet-bound, the next logical step is to move your security and controls to the cloud as well. By implementing bandwidth management, you can enforce application prioritization policies in the cloud across your organization from a single console, without any hardware or software to deploy or manage, eliminating bottlenecks and reducing costs associated with traditional solutions.
WAN Bandwidth
As we’ve previously discussed, network transformation helps you control and remove costs incurred as a result of backhauling internet traffic across the WAN from the branches. A 30% impending annual increase in internet traffic affects all lines of connectivity between users and their destinations. Therefore, if a user is traveling across a WAN link to the data center for egress, that WAN link is subject to the same 30% CAGR. It is helpful at this stage to analyze how much of your WAN traffic is internet bound and ascertain when and which upgrades should be considered.
If you are considering a hybrid network with both MPLS and ISP connectivity at the branches, you can eliminate the need for future MPLS circuit upgrades because you will no longer be backhauling the internet traffic that impacts your WAN demand growth. As your applications and services move from your data centers to the cloud, there is less traffic traversing to and from the data center. Your MPLS costs can stay flat or be reduced. For organizations considering an internet-only approach for some branches, MPLS can be eliminated in favor of low-cost internet connections. Through network transformation, you can avoid the need to upgrade your existing WAN circuits and reduce the required bandwidth of WAN circuits as a result of off-loading internet traffic to local ISP circuits.
Business Value Justification
Let’s turn to a value creation model to quantify the positive economic benefits of secure cloud transformation. The methodology and output should help you derive the business value justifications required to navigate through the steps of your transformation journey.
This model was constructed to represent a typical network transformation project for an enterprise organization with 5,000 users at 50 branch locations. The model assumes that, before the completion of the branch transformation project, all branches backhaul internet traffic to one of six regional or centralized data centers. Each data center in the model has an internet egress gateway consisting of four web security appliances, four SSL inspection appliances, and two internal next-generation firewalls. Also, the model estimates an average WAN connectivity cost of USD $2,400 per month for each branch.
Summary of value creation model assumptions:
- 5,000 users
- 50 branch locations
- Average WAN cost of USD $2,400 per month per branch (20mbps)
- All branches backhaul internet traffic to one of 6 data centers
- The six data center gateways include (in total):
• 24 web security appliances (USD $432K annual)
• 24 SSL inspection appliances (USD $324K annual)
• 12 internal next-generation firewalls (USD $108K annual)
• Hosting costs (USD $60K annual)
- 50% of WAN traffic is going to the internet
- Internet consumption is growing at an annual rate of 30% (CAGR)
- Cost of internet connectivity 15% relative to the cost of MPLS
- Network transformation project is complete
- This example covers hard costs only—vendor-specific investment costs are not included
Based on the value assessment model, here’s an example of how your organization could benefit from cloud transformation.
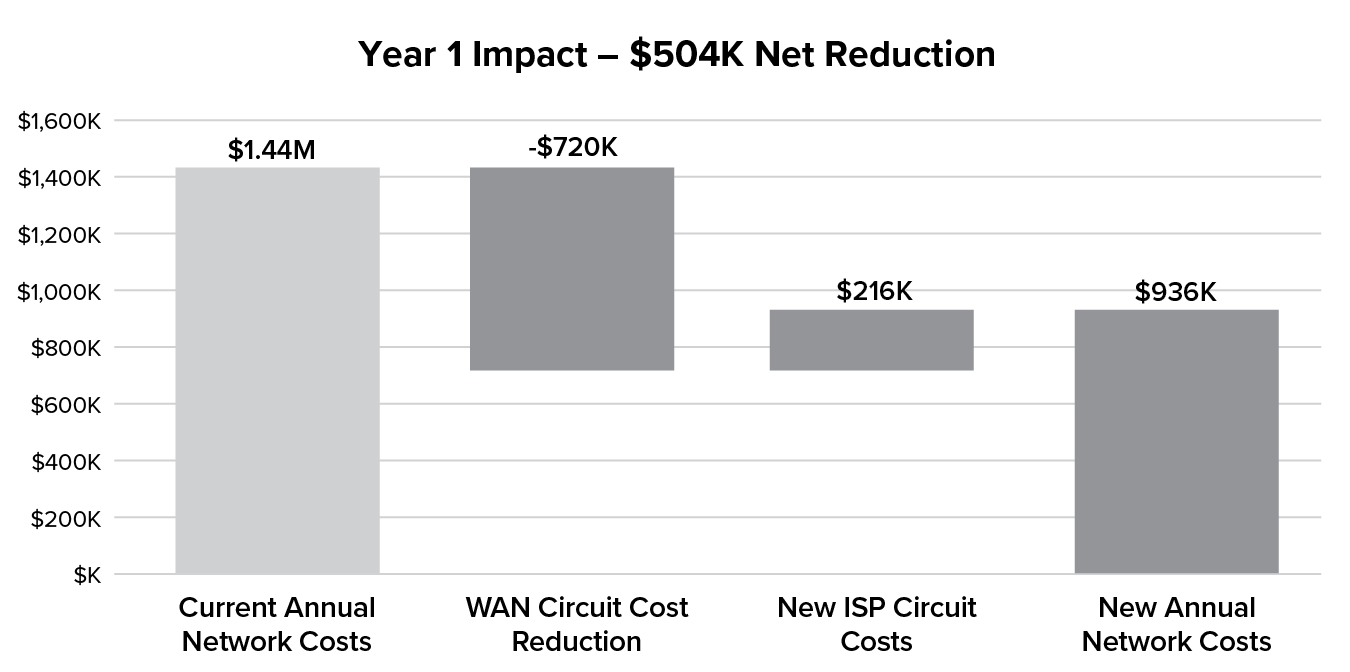
Figure 10.1 Year 1 net impact as a result of transformation
Figure 10.1 illustrates how the current-state hard costs are reduced by replacing traditional WAN circuits with lower-cost internet circuits that provide more available bandwidth. The starting point of USD $1.44M annual run rate of WAN costs is reduced by USD $720K through the MPLS circuit reductions. The additional USD $216K cost for internet connections results in a net impact of USD $504K per year, lowering the overall run rate to USD $936K (a 35% reduction in costs).
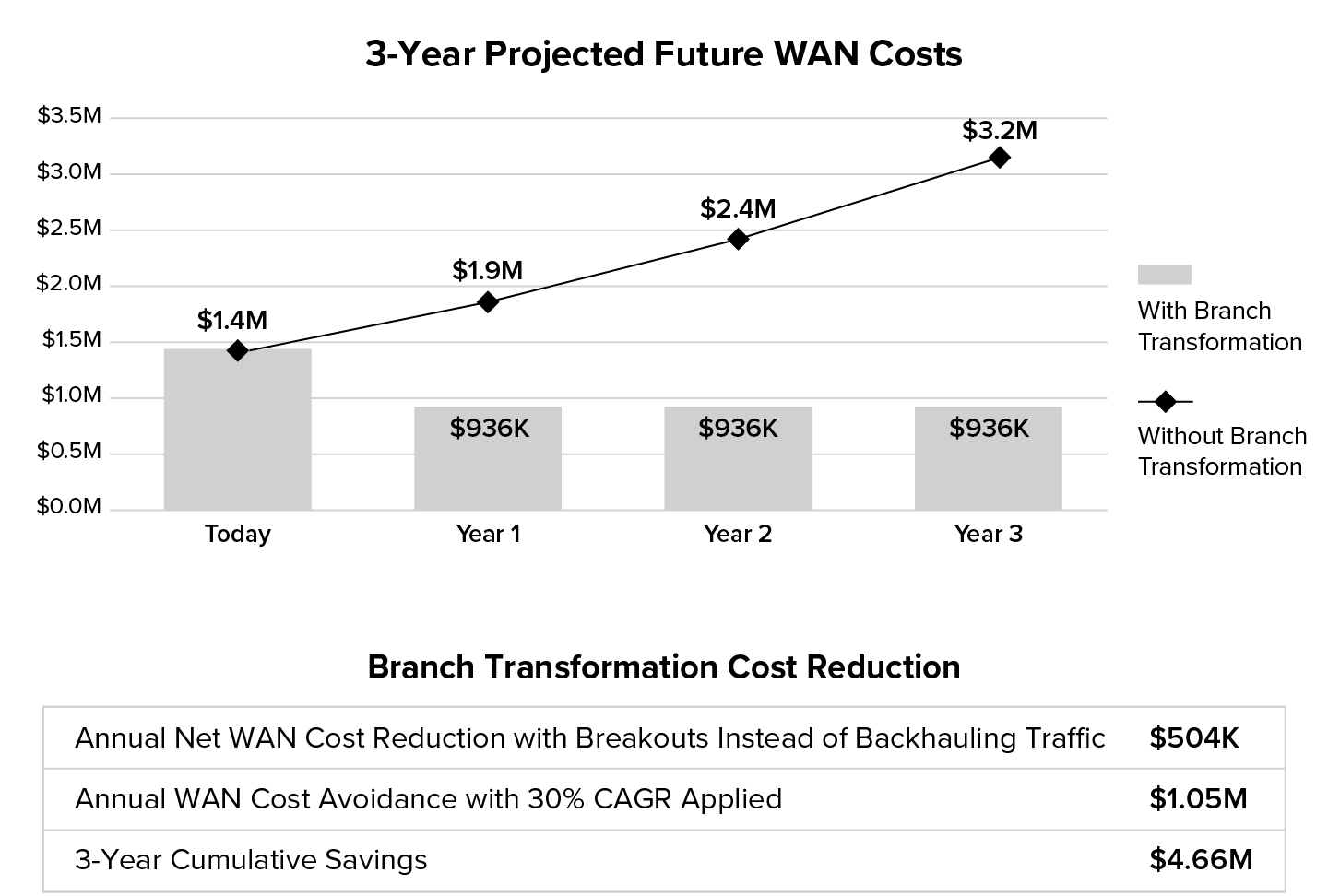
Figure 10.2 Three-year WAN cost projection comparing costs as-is vs. cost savings from branch network transformation.
Without branch transformation, the existing WAN circuits are subject to 30% compound annual growth rates as a result of increased internet demand from further adoption of cloud and SaaS. However, with branch transformation, the benefits realized in the first full year post-network transformation alone will carry over year-over-year. Implementing additional capabilities such as bandwidth control can help mitigate the 30% CAGR. This results in a USD $2.23M delta three years out, and a three-year cumulative savings of $4.66M or 62% of what would otherwise have been spent over those three years if not for transformation, as illustrated in Figure 10.2.
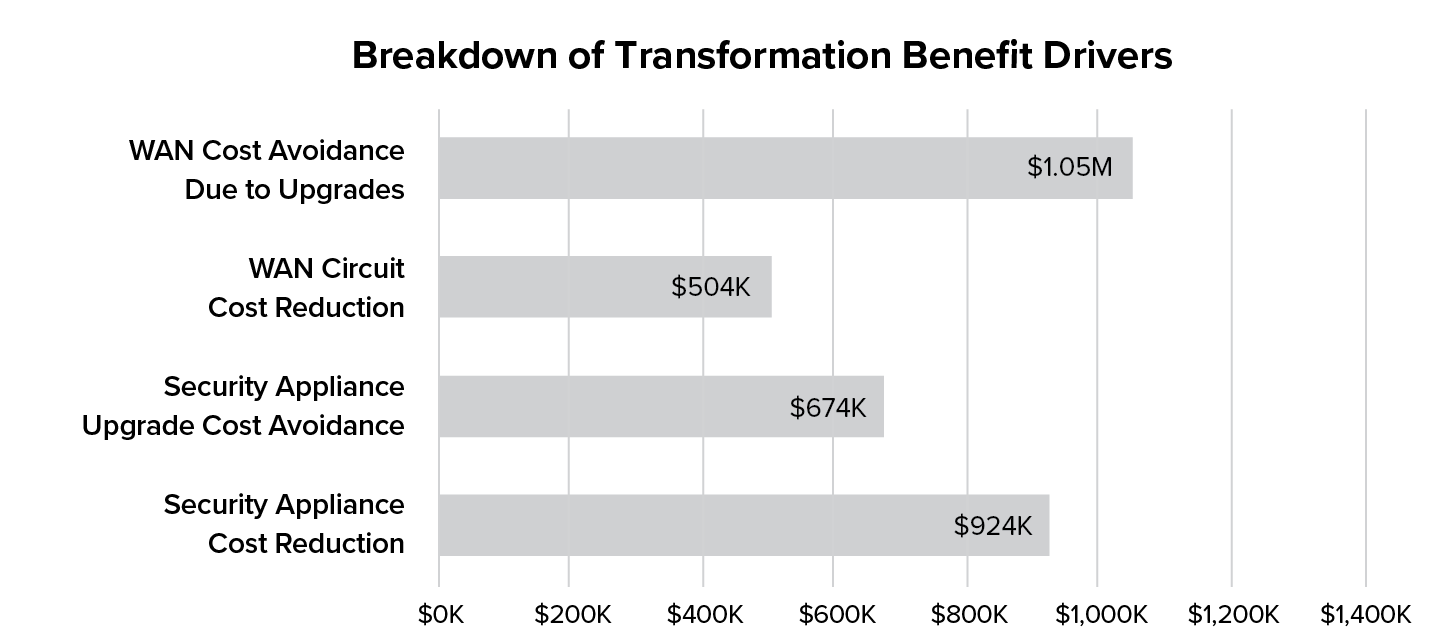
Figure 10.3 Annual cost benefits breakdown of network and security transformation (over 3 years)
On the network side, future WAN costs can be avoided by mitigating the 30% internet consumption CAGR and through the reduction of current WAN costs by eliminating backhaul as seen in Figure 10.3. With security transformation the same 30% internet consumption CAGR that would normally require in-place upgrades or more frequent hardware refreshes can be avoided, while existing security appliances are displaced through simplification in the cloud.
In this model, security transformation removes 24 web proxy appliances, 24 SSL inspection appliances, and 12 outbound firewalls across the six data centers. The removed hard costs include hardware (annualized capital expenditure depreciation), software, licensing, and annual vendor maintenance. Soft costs that would include contractor and device management costs associated with managing the legacy security infrastructure such as incident management, break/fix, and so on, are not factored in this model due to the considerable variability of these costs from scenario to scenario.
Chapter 10 Takeaways
- Secure cloud transformation creates business value by both driving top line growth and improving the bottom line.
- In addition to enabling cloud transformation, network transformation yields significant cost savings of its own, making you not only an enabler of business outcomes but also a hero to the bottom line.
- Engaging in a comprehensive business value analysis early on in the process helps to map the organization’s business goals to the benefits cloud transformation offers. It also provides a structured approach for evaluating all the considerations that accompany a move to the cloud.
- A value creation framework helps organizations better understand the impact of their cloud transformation journey across multiple dimensions. Such a framework can also identify secondary benefits that exist beyond the immediate IT impact, e.g., any hidden on-premises hardware costs, factor in the impact of highly variable soft costs such as personnel and management costs that are typically not incorporated into a hard cost TCO model.
- A value creation analysis can also help the company set a timetable for transformation and identify options and steps to derive cost savings as well as cost avoidance.